Azure for Active Directory: 7 Powerful Benefits You Can’t Ignore
Thinking about upgrading your identity management? Azure for Active Directory isn’t just a buzzword—it’s a game-changer. Seamlessly blending cloud efficiency with enterprise-grade security, it’s reshaping how businesses manage access, identities, and compliance in a hybrid world.
What Is Azure for Active Directory?

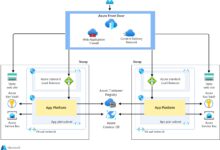
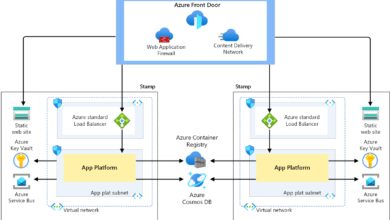
Azure for Active Directory, commonly known as Azure AD, is Microsoft’s cloud-based identity and access management service. It enables organizations to securely manage user identities, control access to applications, and enforce conditional access policies across cloud and on-premises environments. Unlike traditional on-prem Active Directory, Azure AD is built for the modern, mobile, and cloud-first workforce.
Core Definition and Purpose
Azure for Active Directory is not simply a cloud version of Windows Server Active Directory. Instead, it’s a modern identity platform that supports web-based authentication protocols like OAuth 2.0, OpenID Connect, and SAML. Its primary function is to provide single sign-on (SSO), multi-factor authentication (MFA), and identity governance for cloud applications such as Microsoft 365, Salesforce, and thousands of other SaaS platforms.
- Centralized identity management across cloud and hybrid environments
- Supports modern authentication standards
- Enables secure access from any device, anywhere
Evolution from On-Prem AD to Cloud Identity
Traditional Active Directory has been the backbone of enterprise identity for decades. However, as businesses shift to cloud services, remote work, and mobile devices, the limitations of on-prem AD—such as scalability, geographic reach, and integration with cloud apps—have become apparent. Azure for Active Directory emerged as the natural evolution, offering a cloud-native solution that integrates with on-prem AD when needed via tools like Azure AD Connect.
“Azure AD is not a replacement for on-prem AD—it’s an extension that empowers organizations to move securely into the cloud.” — Microsoft Identity Documentation
Key Features of Azure for Active Directory
Azure for Active Directory offers a robust suite of features designed to enhance security, streamline user management, and improve user experience. These capabilities make it a cornerstone of modern IT infrastructure.
Single Sign-On (SSO) Across Applications
One of the most impactful features of Azure for Active Directory is its ability to provide seamless single sign-on to thousands of pre-integrated SaaS applications. Users can log in once and gain access to all their authorized apps without re-entering credentials.
- Supports over 2,600 pre-integrated applications via the Azure AD Application Gallery
- Custom app integration using SAML, OAuth, or password-based SSO
- Reduces password fatigue and improves productivity
For example, a user logging into their corporate laptop can automatically access Microsoft 365, Dropbox, Workday, and Zoom without additional logins. This is made possible through federation and token-based authentication managed by Azure AD. Learn more about app integration at Microsoft’s official app management guide.
Multi-Factor Authentication (MFA)
Security is paramount, and Azure for Active Directory delivers with robust Multi-Factor Authentication. MFA requires users to verify their identity using at least two of the following: something they know (password), something they have (phone or token), or something they are (biometrics).
- Available via phone call, text message, Microsoft Authenticator app, or FIDO2 security keys
- Can be enforced based on risk, location, or device compliance
- Reduces the risk of account compromise by up to 99.9%
According to Microsoft, accounts with MFA enabled are nearly immune to common phishing and credential-stuffing attacks. Organizations can configure MFA policies through the Azure portal or integrate them with Conditional Access rules for fine-grained control.
Conditional Access and Risk-Based Policies
Conditional Access is a powerful capability within Azure for Active Directory that allows IT administrators to enforce access controls based on specific conditions. These policies can require MFA, block access from untrusted locations, or restrict access to compliant devices.
- Define policies based on user, group, application, device state, location, and risk level
- Integrate with Microsoft Defender for Identity for real-time threat detection
- Supports “block” or “require MFA” actions dynamically
For instance, a policy can be set to block logins from outside the corporate network unless the user is on a company-managed device and has completed MFA. This level of control is essential for zero-trust security models. More details can be found at Microsoft’s Conditional Access documentation.
Integration Between Azure for Active Directory and On-Premises AD
Most enterprises still rely on on-premises Active Directory for legacy systems, file servers, and internal applications. Azure for Active Directory doesn’t require a complete migration—it integrates seamlessly with existing infrastructure through synchronization and hybrid identity models.
Using Azure AD Connect for Synchronization
Azure AD Connect is the primary tool used to synchronize user identities, passwords, and group memberships from on-premises Active Directory to Azure AD. This ensures that users have a consistent identity across both environments.
- Supports password hash synchronization, pass-through authentication, and federation
- Allows for seamless user experience with single password for on-prem and cloud
- Can be deployed on a dedicated server within the corporate network
Organizations can choose the authentication method that best fits their security and operational requirements. For example, pass-through authentication validates user credentials directly against on-prem AD without storing password hashes in the cloud, enhancing security.
Hybrid Identity Scenarios and Best Practices
Hybrid identity is a common deployment model where organizations maintain on-prem AD while extending identity to the cloud via Azure for Active Directory. This approach supports gradual cloud adoption without disrupting existing workflows.
- Best practice: Use Azure AD Connect with pass-through authentication and seamless SSO
- Monitor sync health using the Azure AD Connect Health service
- Plan for redundancy by deploying multiple sync servers in large environments
Microsoft recommends enabling seamless SSO so users don’t need to re-enter credentials when accessing cloud resources from domain-joined devices. This improves user experience while maintaining security. More guidance is available at Microsoft’s hybrid identity documentation.
Security and Compliance in Azure for Active Directory
With cyber threats on the rise, identity has become the new security perimeter. Azure for Active Directory provides advanced security features that help organizations detect, prevent, and respond to identity-based attacks.
Identity Protection and Risk Detection
Azure AD Identity Protection uses machine learning and risk signals to detect suspicious sign-in behaviors, such as logins from anonymous IPs, unfamiliar locations, or impossible travel. It assigns a risk level (low, medium, high) to each sign-in attempt.
- Automatically flags risky sign-ins and user accounts
- Can trigger automated responses like requiring password reset or blocking access
- Integrates with Conditional Access to enforce risk-based policies
For example, if a user typically logs in from New York and suddenly attempts to sign in from Russia within an hour, Identity Protection flags this as “impossible travel” and can require MFA or block the attempt. This proactive defense is critical in preventing account takeovers.
Privileged Identity Management (PIM)
Privileged accounts are high-value targets for attackers. Azure AD Privileged Identity Management (PIM) helps secure these accounts by enabling just-in-time (JIT) access and time-bound role activation.
- Administrators must request and justify access to elevated roles
- Access can be limited to a specific time window (e.g., 4 hours)
- Full audit trail of who accessed what and when
PIM supports roles like Global Administrator, SharePoint Administrator, and more. By minimizing standing privileges, organizations reduce the attack surface and comply with regulatory requirements like GDPR, HIPAA, and SOX.
Compliance and Audit Logging
Azure for Active Directory provides comprehensive audit logs that track user activities, sign-ins, and administrative changes. These logs are essential for compliance reporting and forensic investigations.
- Sign-in logs show IP addresses, device info, and authentication methods
- Audit logs capture configuration changes, role assignments, and app consent
- Logs can be exported to SIEM tools like Microsoft Sentinel or Splunk
Organizations can set up alerts for suspicious activities, such as multiple failed logins or admin role changes. The ability to generate compliance reports helps meet audit requirements and demonstrate due diligence.
Deployment Models and Licensing Options
Azure for Active Directory offers multiple deployment models and licensing tiers to suit different organizational needs, from small businesses to large enterprises.
Free vs. Premium Tiers (P1 and P2)
Azure AD comes in four editions: Free, Office 365 apps, Premium P1, and Premium P2. The Free edition includes basic SSO and MFA, while P1 and P2 unlock advanced features.
- Free: User management, basic SSO, MFA for admins
- Premium P1: Includes Conditional Access, hybrid identity, and self-service password reset
- Premium P2: Adds Identity Protection, PIM, and access reviews
Most enterprises opt for P1 or P2 to leverage security and governance features. Licensing is typically per user per month and can be bundled with Microsoft 365 subscriptions.
Choosing the Right Deployment Strategy
Selecting the right deployment model depends on factors like existing infrastructure, security requirements, and cloud adoption goals.
- Cloud-only: For organizations fully migrated to the cloud with no on-prem AD
- Hybrid: For businesses with legacy systems and gradual cloud migration
- Federated: For organizations using ADFS and requiring SSO with external partners
Microsoft recommends starting with password hash synchronization and MFA, then gradually adopting Conditional Access and Identity Protection as maturity increases. A phased approach reduces risk and allows for user training and policy refinement.
User Management and Self-Service Capabilities
Azure for Active Directory empowers users and reduces IT overhead through self-service features that allow users to manage their own identities securely.
Self-Service Password Reset (SSPR)
One of the most widely used features in Azure for Active Directory is Self-Service Password Reset. It allows users to reset their passwords or unlock their accounts without calling the helpdesk.
- Users can authenticate via email, phone, or security questions
- Can be enabled for both cloud and on-prem AD accounts (with sync)
- Reduces helpdesk costs by up to 40%
SSPR improves user productivity and reduces the burden on IT teams. Organizations can customize the registration process and enforce strong authentication methods.
Access Reviews and Role Management
Access reviews help ensure that users have the right level of access over time. Administrators can schedule periodic reviews of group memberships, app access, and role assignments.
- Reviewers (managers or owners) approve or remove access
- Automated reminders and escalation workflows
- Supports compliance with least-privilege principles
Role management in Azure AD allows for granular delegation of administrative tasks. Instead of granting full Global Admin rights, organizations can assign roles like Helpdesk Admin or Billing Admin with limited scope.
Monitoring, Reporting, and Troubleshooting
Effective identity management requires continuous monitoring and the ability to troubleshoot issues quickly. Azure for Active Directory provides built-in tools for visibility and diagnostics.
Sign-In Logs and Audit Trails
The Azure portal includes detailed sign-in logs that show every authentication attempt, including success, failure, and risk levels. These logs are crucial for investigating security incidents.
- Filter by user, app, IP address, or time range
- View detailed error codes (e.g., 50058 for certificate issues)
- Export logs to CSV or integrate with Log Analytics
For example, if users report login issues, administrators can check the sign-in logs to identify patterns—such as MFA failures or blocked locations—and resolve them quickly.
Using Azure Monitor and Log Analytics
For advanced monitoring, Azure for Active Directory integrates with Azure Monitor and Log Analytics. This allows organizations to create custom dashboards, set up alerts, and perform deep analysis of identity data.
- Monitor sync health, MFA usage, and Conditional Access policy effectiveness
- Create alerts for unusual spikes in failed logins
- Correlate identity events with other security data
By sending Azure AD logs to Log Analytics, enterprises gain a unified view of their security posture. More information is available at Microsoft’s monitoring documentation.
Troubleshooting Common Issues
Despite its reliability, Azure for Active Directory can encounter issues such as sync errors, MFA timeouts, or Conditional Access blocks.
- Synchronization issues: Check Azure AD Connect server status and connectivity
- MFA not working: Verify user registration and authentication methods
- Access denied: Review Conditional Access policies and user compliance
Microsoft provides troubleshooting guides and the Azure AD Connect Health tool to diagnose and resolve common problems. Proactive monitoring can prevent outages and ensure business continuity.
Future Trends and Innovations in Azure for Active Directory
Azure for Active Directory continues to evolve with new features that align with modern security and identity trends.
Passwordless Authentication and FIDO2
Microsoft is pushing toward a passwordless future. Azure for Active Directory now supports FIDO2 security keys, Windows Hello, and the Microsoft Authenticator app as primary authentication methods.
- Eliminates reliance on passwords, reducing phishing risk
- Users sign in with biometrics or hardware tokens
- Supported on modern devices and browsers
Organizations can enable passwordless for employees, improving both security and user experience. More details at Microsoft’s passwordless guide.
Integration with Microsoft Entra ID
In 2023, Microsoft rebranded Azure AD to Microsoft Entra ID as part of a new identity security portfolio. While the core functionality remains the same, this rebrand reflects a broader vision for zero-trust identity.
- Entra ID includes Azure AD, Conditional Access, Identity Protection, and more
- Emphasizes identity as the primary security boundary
- Future updates will focus on AI-driven threat detection and automation
Existing Azure for Active Directory users will transition smoothly, but the rebrand signals Microsoft’s commitment to advancing identity security.
AI and Machine Learning in Identity Security
AI is playing an increasing role in detecting anomalies and predicting threats. Azure for Active Directory uses machine learning in Identity Protection to analyze sign-in patterns and flag suspicious behavior.
- Adaptive authentication adjusts requirements based on risk
- Automated investigations reduce response time
- Future enhancements may include behavioral biometrics
As AI capabilities grow, Azure AD will become even smarter at preventing breaches before they happen.
What is Azure for Active Directory?
Azure for Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. It enables secure user authentication, single sign-on, and access control for cloud and on-premises applications. It is not a direct replacement for on-prem Active Directory but works alongside it in hybrid environments.
How does Azure AD integrate with on-premises Active Directory?
Azure AD integrates with on-premises AD using Azure AD Connect, which synchronizes user identities and passwords. Organizations can choose synchronization methods like password hash sync, pass-through authentication, or federation to maintain a seamless identity experience.
What are the differences between Azure AD Free, P1, and P2?
Azure AD Free includes basic SSO and MFA for admins. P1 adds Conditional Access, hybrid identity, and self-service password reset. P2 includes advanced security features like Identity Protection and Privileged Identity Management (PIM).
Is Azure AD the same as Microsoft Entra ID?
Yes, Azure AD has been rebranded as Microsoft Entra ID. The core functionality remains the same, but the new name reflects Microsoft’s broader identity security vision under the Entra product family.
Can Azure AD replace on-prem Active Directory?
While Azure AD can support cloud-only environments, most enterprises use it in conjunction with on-prem AD for legacy systems. A full replacement is possible but requires careful planning and application compatibility assessment.
Adopting Azure for Active Directory is no longer just an IT upgrade—it’s a strategic move toward enhanced security, operational efficiency, and digital transformation. From seamless single sign-on and robust MFA to advanced threat protection and compliance tools, Azure for Active Directory empowers organizations to manage identities in a modern, hybrid world. Whether you’re just starting your cloud journey or optimizing an existing setup, leveraging Azure for Active Directory can future-proof your identity infrastructure and support a secure, productive workforce.
Recommended for you 👇
Further Reading: